Describe the Security Issues Surrounding the Use of Computer Networks
Debra Littlejohn Shinder MCSE MVP Security is a technology consultant trainer and writer who has authored a number of books on. Identify the need for encryption authentication techniques including the use of user identification and passwords when using common network.
What Is Information Securtiy Policy Principles Threats Imperva
Computer and network security is essentially a battle of wits between a perpetrator who tries to find holes and the designer or administrator who tries to close them.

. To that end proactive network managers know they should routinely examine their security infrastructure and related best practices in order to upgrade accordingly. Such an approach can make a difference in the ability to effectively respond to the following five network security threats. De George 338 This part of our discussion will focus primarily on.
The use of the Internet and other computer networks has seen explosive growth. Lack of physical security controls. O describe other issues such as the internet is not policed and the effects of this such as the existence of inappropriate sites.
Network security issues involve maintaining network integrity preventing unauthorized users from infiltrating the system viewingstealing sensitive data passwords etc and protecting the network denial of service attacks. Guest post written by Tom Cross Tom Cross is director of security research at Lancope a security software firm. A firewall is a networking security tool that can be configured to block certain types of network access and data from leaving the network or being accessed from outside of the network.
Remote access client devices may be used in hostile environments but not. These could be harmless adware or dangerous trojan infection. A properly configured firewall is necessary for network security and while many modems include this its often not robust enough for business use.
A look at the top security threats facing wireless networks and computer software in 2013 as laid out by cyber security software makers Kaspersky Lab. Discuss the problems of confidentiality and security of data including problems surrounding common network environments. Viruses spam network intrusions and denial-of-service attacks are just a few examples of the threats in existence today that can adversely affect a companys network.
Despite the many benefits of using networks networking raises a greater potential for security issues such as. Computer security threats are potential threats to your computers efficient operation and performance. As soon as your computer is connected to a network you have to start thinking about security security of your files information etc.
It does not encompass a complete discussion of all the issues surrounding the topics in an investigation and does not attempt to provide guidance on traditional investigative procedures. If your computer is connected to a network other people can connect to your computer. 2 responsibility for computer failure.
Malicious attacks such as hacking and viruses. And 4 privacy of the company workers and customers. You can implement measures to reduce your networks.
Exposure is different than vulnerability. With the increased use of the Internet comes an increased risk of a businesss computer network being affected by malicious programs such as viruses. Remote access client devices generally have weaker protection than standard client devices.
A computer virus is a piece of computer code that is inserted into another program and lies dormant until triggered by. Trojan Horse A program designed to breach the security of a computer system while. Encryption is a double-edged sword.
An exposure could enable a hacker to harvest sensitive information in a covert manner. The great advantage that the attacker has is that he or she need only find a single weakness while the designer must find and eliminate all weaknesses to achieve perfect security. Many devices not managed by the enterprise No enterprise firewalls antivirus etc.
Up to 24 cash back 42 network issues and communication security issues regarding data transfer describe the security issues surrounding the use of computer networks describe other issues such as the idea that the internet is not policed and the effects of this such as the existence of inappropriate sites. The Worlds Largest Repository of Historical DNS data. Worms typically cause harm to their host networks by consuming bandwidth and overloading web servers.
They are 1 computer crime. Client devices in many types of environments. It provides a malicious actor with indirect access to a system or a network.
O describe the security issues surrounding the use of computer networks. These issues are greatly magnified as a networks increases in size. A network allows a person who does to have physical access to your computer they are not sitting in front of it to gain access all the same.
Three main threats facing computer network security include. Tom Cross With each passing year the security threats facing computer networks. Abstract- The rapid development in computer network technology leads to the security challenges faced by it at every step of its growth.
O identify methods of avoiding password interception such as the use of anti spyware and changing passwords regularly. Up to 24 cash back Computer Worm A standalone malware computer program that replicates itself in order to spread to other computers Exploit operating system vulnerabilities. Resources sharing data communication computer virus and TCPIP.
Involving the use of the Internet and other computer networks. Describe other common network devices including hubs bridges switches and proxy servers. A threat in a computer system is a potential danger that could jeopardize your data security.
3 protection of computer property records and software. As the world becomes more digital computer security concerns are always developing. Safety factors of the network are mainly.
Network Security and Preserving Network Integrity Modern enterprises are constantly at odds with various security issues their networks face on a daily basis. Hackers computer virus and denial of service attack.
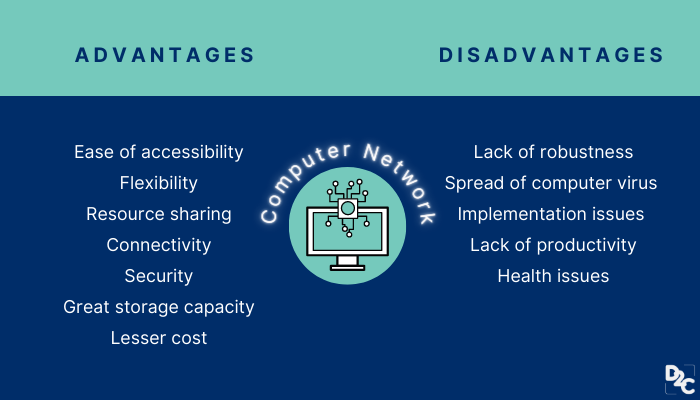
Advantages And Disadvantages Of Computer Network D2c

Cybersecurity Vs Information Security Vs Network Security

Computer Networks And Its Types Basics Of Computer Networking With Functions
![]()
What Is Network Security The Different Types Of Protections Check Point Software
What Is Computer Security Introduction To Computer Security

What Is Network Security Fundamentals Of Network Security
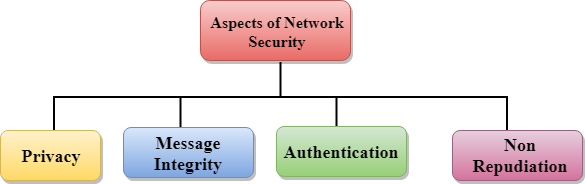
Computer Network Security Javatpoint
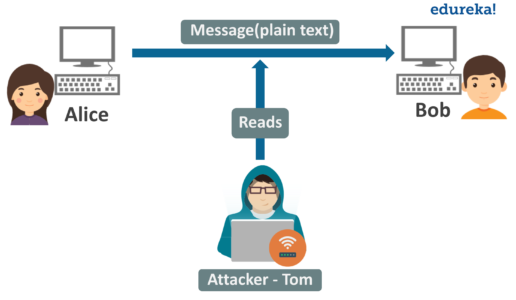
What Is Network Security Fundamentals Of Network Security

215 Questions With Answers In Computer Networking Science Topic
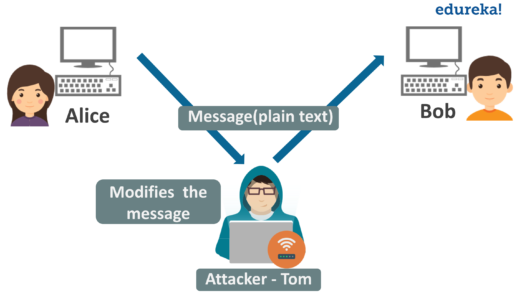
What Is Network Security Fundamentals Of Network Security

Pdf Computer Network Development To Achieve Resource Sharing

Top 60 Networking Interview Questions And Answers

What Is Network Security And Why Is It Important

7 Types Of Cyber Security Threats

What Is Computer Security Introduction To Computer Security
Computer Network Advantages And Disadvantages 6 Valuable Differences

Network Security Threats 5 Ways To Protect Yourself

What Is A Computer Security Risk Definition Types Video Lesson Transcript Study Com

Comments
Post a Comment